What is Azure AD Privileged Identity Management?
- The Tech Platform

- Jun 24, 2020
- 2 min read
Azure Active Directory (Azure AD) Privileged Identity Management (PIM) is a service that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services like Office 365 or Microsoft Intune.
Reasons to use
Organizations want to minimize the number of people who have access to secure information or resources, because that reduces the chance of a malicious actor getting that access, or an authorized user inadvertently impacting a sensitive resource. However, users still need to carry out privileged operations in Azure AD, Azure, Office 365, or SaaS apps. Organizations can give users just-in-time (JIT) privileged access to Azure resources and Azure AD. There is a need for oversight for what those users are doing with their administrator privileges.
What does it do?
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
Provide just-in-time privileged access to Azure AD and Azure resources
Assign time-bound access to resources using start and end dates
Require approval to activate privileged roles
Enforce multi-factor authentication to activate any role
Use justification to understand why users activate
Get notifications when privileged roles are activated
Conduct access reviews to ensure users still need roles
Download audit history for internal or external audit
What can I do with it?
Once you set up Privileged Identity Management, you'll see Tasks, Manage, and Activity options in the left navigation menu. As an administrator, you'll choose between managing Azure AD roles and Azure resource roles. When you choose the type of roles to manage, you see a similar set of options for that role type.
Who can do what?
For Azure AD roles in Privileged Identity Management, only a user who is in the Privileged role administrator or Global administrator role can manage assignments for other administrators. You can grant access to other administrators to manage Privileged Identity Management. Global Administrators, Security Administrators, Global readers, and Security Readers can also view assignments to Azure AD roles in Privileged Identity Management.
For Azure resource roles in Privileged Identity Management, only a subscription administrator, a resource Owner, or a resource User Access administrator can manage assignments for other administrators. Users who are Privileged Role Administrators, Security Administrators, or Security Readers do not by default have access to view assignments to Azure resource roles in Privileged Identity Management.
Scenarios
Privileged Identity Management supports the following scenarios:
Privileged Role administrator permissions
Enable approval for specific roles
Specify approver users or groups to approve requests
View request and approval history for all privileged roles
Approver permissions
View pending approvals (requests)
Approve or reject requests for role elevation (single and bulk)
Provide justification for my approval or rejection
Eligible role user permissions
Request activation of a role that requires approval
View the status of your request to activate
Complete your task in Azure AD if activation was approved
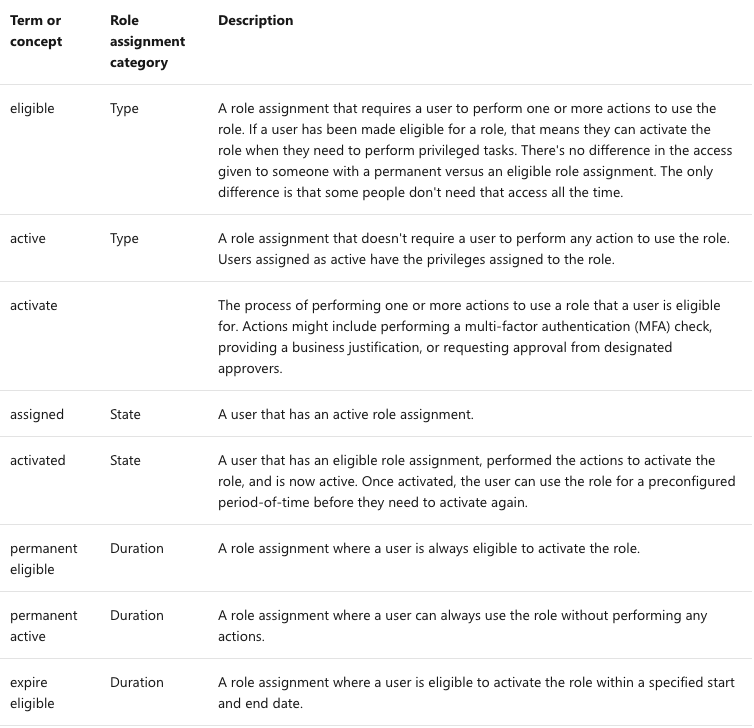
Terminology
To better understand Privileged Identity Management and its documentation, you should review the following terms.
License requirements
Using this feature requires an Azure AD Premium P2 license. To find the right license for your requirements, see Comparing generally available features of the Free, Basic, and Premium editions.
For information about licenses for users, see License requirements to use Privileged Identity Management.
Source: Paper.li







Comments