As a defense evasion technique, adversaries change features of their malicious artifacts with legitimate and trusted ones. Code signatures, names and location of malware files, names of tasks and services are some examples of these features. After masquerading, malicious artifacts of adversaries such as malware files appear legitimate to users and security controls.
In this article, we review:
the fundamentals of the Masquerading technique
features manipulated by adversaries for Masquerading
its use cases by threat actors and malware
Red team exercises for this technique
Introduction
Adversaries masquerade their malicious artifacts, such as malware files and processes, as legitimate software and processes to evade detection by users and security controls.
Masquerading Sub-techniques
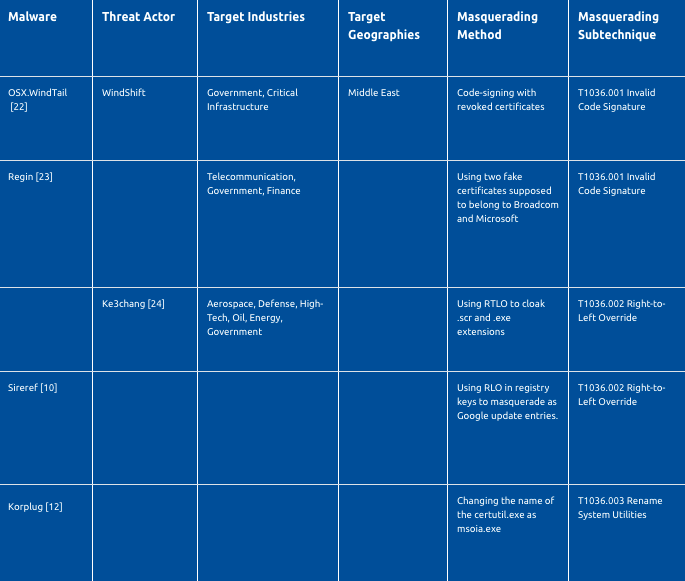
1.T1036.001 Invalid Code Signature
Code signing is the process of digitally signing executables to verify the author of the program and guarantee that the code has not been tampered with. In the invalid code signature sub-technique, adversaries copy metadata and code signature information of valid and signed programs and use this information in their malware.
Since a code signature is valid for a specific program, it is not valid for any other programs. Therefore, unlike the Code Signing sub-technique of the T1553 Subvert Trust Controls ATT&CK technique [1], this code signature cloning activity for masquerading will not result in a valid signature. So, although these malware files appear more legitimate to users, security analysts and security controls, they cannot pass digital signature validation.
MetaTwin is an open-source tool that copies metadata and AuthentiCode signature from one file and injects it into another [2]. MetaTwin extracts the resources of a legitimate binary using the Resource Hacker tool [3]. It also extracts the digital signature information of the legitimate binary with the SigThief tool [4]. Then, MetaTwin writes the extracted metadata and digital signature information to a target binary
2. T1036.002 Right-to-Left Override
Right-to-left override (RTLO or RLO) character is a non-printing Unicode character (U+202E) that is used to display the text that follows it in right-to-left order. This special character is used to deal with languages that are written from right-to-left and causes the text that follows it to be displayed in reverse. For example, the file name receiptU+202Etxt.exe will appear on the screen as receiptexe.txt. Users may think that the file is a text file, but it is actually an executable file. As another example, the filename with receiptmcod.txt may be actually receipt\u202Etxt.docm, which is a macro-enabled document file with a U+202e placed just before mcod.txt. Note that this operation only changes the visual appearance of the file name, does not change the actual file name – it still has the extension docm.
This feature (!) is used by adversaries to trick users into opening malware files by showing the file extension as a benign extension instead of executable. This Masquerading sub-technique is commonly used with the Malicious File sub-technique of the T1204 User Execution ATT&CK technique [5] and Spearphishing Attachment sub-technique of the T1566 Phishing ATT&CK technique [6].
Etumbot backdoor malware leverages the Unicode Right-to-Left Override (RLO) technique combined with convincing icons for various types of PDFs or Microsoft Office documents to trick the user into clicking and executing the malware file delivered via spearphishing [7].
As a recent example, an APT group used the RLO technique to disguise an SCR (Windows screensaver) malware as a document file [8]. Adversaries also used a classic Right-to-Left Override attack to trick Telegram users by changing displayed file extension [9]. For example, a JS malware file is renamed as follows: my_photo_U+202Egnp.js Where U+202E is the RLO character to make Telegram display the remaining string gnp.js in reverse, sj.png. Then, the adversary sends the message, and the recipient sees an incoming PNG image file instead of a JS JavaScript file.
RLO/RTLO can be used in the Windows Registry as well. For example, Sirefef malware uses the RLO technique to trick users into believing that the entries it creates in the registry of the infected machine are legitimate Google update entries [10].
3. T1036.003 Rename System Utilities
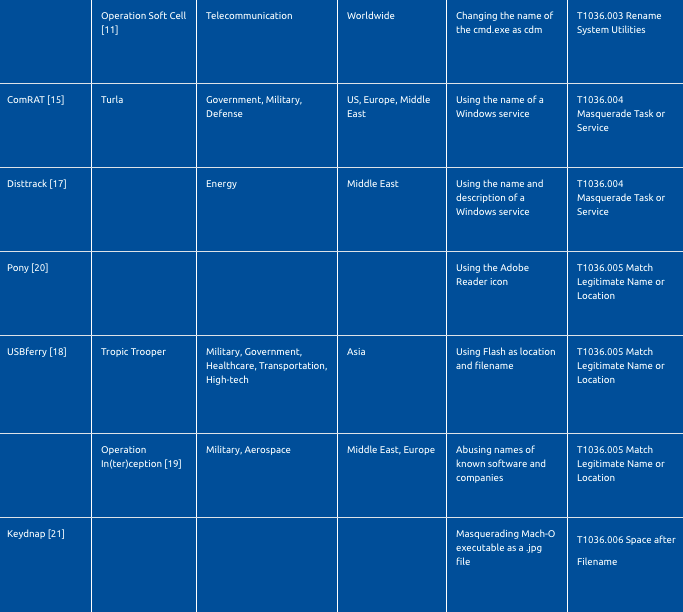
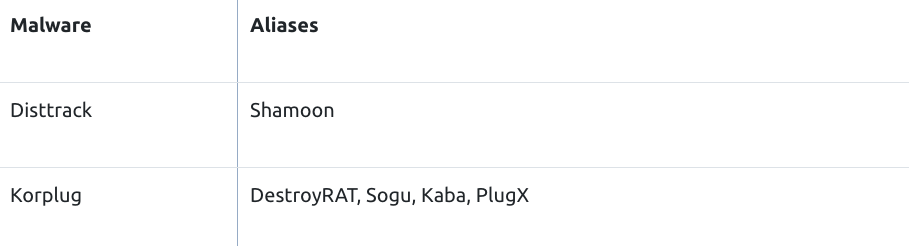
Adversaries frequently utilize Windows system utilities in their operations to bypass defensive security controls. Rundll32.exe, cmd.exe, and certutil.exe are some of these utilities. Because of the increased use of legitimate system utilities by adversaries, security tools may monitor them to detect their suspicious use. To avoid name-based detection, adversaries may rename system utilities. For example, threat actors of Operation Soft Cell changed the name of the cmd.exe as cdm.exe [11]. Korplug malware, which is leveraging the COVID-19 pandemic to spread, is using a renamed certutil.exe - msoia.exe to decode the CAB file [12].
4.T1036.004 Masquerade Task or Service
Adversaries use task and service functionalities of operating systems to facilitate initial or recurring execution of their malicious code [13] [14]. As a part of execution and persistence, malware may create tasks and services to be executed at system startup or repeatedly.
Security controls may quickly detect custom-named tasks and services. Therefore, threat actors masquerade the name of a task/service with the name of a legitimate task/service to make it appear benign and evade detection. Adversaries commonly use identical or similar names of legitimate tasks/services executed by the Windows Task Scheduler, at (Linux and Windows), Windows services, and Linux systemd services.
They may use the name of a Windows service or a legitimate third-party service. For example, ComRAT has used WSqmCons, a name associated with Windows SQM Consolidator [15]. Fin7 has disguised its scheduled tasks as AdobeFlashSync for persistence [16]. In addition to names, adversaries may masquerade descriptions of their tasks/services. For example, Disttrack wiper malware has created a service named ntssrv, with a display name of “Microsoft Network Realtime Inspection Service” and a description of “Helps guard against time change attempts targeting known and newly discovered vulnerabilities in network time protocols” [17].
5. T1036.005 Match Legitimate Name or Location
Adversaries may masquerade names/locations of their artifacts as identical or similar names/locations of legitimate files to evade monitoring and detection. As a recent example, the Tropic Trooper cyberespionage group has used %USERPROFILE%\Documents\Flash\ folder to place its USBferry malware and masquerade its name as flash_en.exe [18]. Threat actors of the Operation In(ter)ception cyberespionage campaign disguised their files and folders by giving them similar names of known software and companies, such as C:\Intel\IntelV.cgi, C:\NVIDIA\NvDaemon.exe, C:\ProgramData\DellTPad\DellTPadRepairexe [19].
Moreover, adversaries change icons of their malware with icons of benign files. As an example, Pony Trojan used a well-known Adobe Reader icon and the filename security or infos to look trustworthy [20].
6. T1036.006 Space after Filename
In macOS, adding a space to the end of a filename will modify how the operating system handles the file with other kinds of files. If an executable Mach-O file is called malware.txt, it will open with the text editing program when double-clicked by a user. So, the executable will not run properly. On the other hand, if the file is renamed as “malware.txt “ (a space added at the end). macOS detects the executable file type and executes the binary when a user double-clicks it.
As an example, OSX / Keydnap backdoor malware was distributed in a zip archive, which contained a binary named “screenshot.jpg“ [21]. Note that the filename contained a space character at its end. Therefore, it would be executed by Terminal.app, and the Keydnap backdoor malware would be run when a user double-clicked it.
Use Cases by Malware and Threat Actors
1
Red and Blue Team Exercises
1. Rename cmd.exe ( T1036.003 Rename System Utilities)
Red Teaming - How to simulate?
In this test, we will copy cmd.exe as cdm.exe like threat actors of Operation Soft Cell [11]:
C:\WINDOWS\system32>copy C:\WINDOWS\System32\cmd.exe C:\WINDOWS\System32\cdm.exe
1 file(s) copiedNow, we can use cdm or cdm.exe instead of cmd or cmd.exe.
Blue Teaming - How to detect?
Following Sigma rule can be used to detect the execution of a renamed binary leveraging new Sysmon OriginalFileName datapoint [25].
title: Renamed Binary
id: 36480ae1-a1cb-4eaa-a0d6-29801d7e9142
status: experimental
description: Detects the execution of a renamed binary often used by attackers or malware leveraging new Sysmon OriginalFileName datapoint.
author: Matthew Green - @mgreen27, Ecco, James Pemberton / @4A616D6573, oscd.community (improvements), Andreas Hunkeler (@Karneades)
date: 2019/06/15
modified: 2019/11/11
references:
- https://attack.mitre.org/techniques/T1036/
- https://mgreen27.github.io/posts/2019/05/12/BinaryRename.html
- https://mgreen27.github.io/posts/2019/05/29/BinaryRename2.html
tags:
- attack.t1036
- attack.defense_evasion
logsource:
category: process_creation
product: windows
detection:
selection:
OriginalFileName:
- 'cmd.exe'
- 'powershell.exe'
- 'powershell_ise.exe'
- 'psexec.exe'
- 'psexec.c' # old versions of psexec (2016 seen)
- 'cscript.exe'
- 'wscript.exe'
- 'mshta.exe'
- 'regsvr32.exe'
- 'wmic.exe'
- 'certutil.exe'
- 'rundll32.exe'
- 'cmstp.exe'
- 'msiexec.exe'
- '7z.exe'
- 'winrar.exe'
- 'wevtutil.exe'
- 'net.exe'
- 'net1.exe'
- 'netsh.exe'
filter:
Image|endswith:
- '\cmd.exe'
- '\powershell.exe'
- '\powershell_ise.exe'
- '\psexec.exe'
- '\psexec64.exe'
- '\cscript.exe'
- '\wscript.exe'
- '\mshta.exe'
- '\regsvr32.exe'
- '\wmic.exe'
- '\certutil.exe'
- '\rundll32.exe'
- '\cmstp.exe'
- '\msiexec.exe'
- '\7z.exe'
- '\winrar.exe'
- '\wevtutil.exe'
- '\net.exe'
- '\net1.exe'
- '\netsh.exe'
condition: selection and not filter
falsepositives:
- Custom applications use renamed binaries adding slight change to binary name. Typically this is easy to spot and add to whitelist
level: medium2. Use a task name similar to a Windows service (T1036.004 Masquerade Task or Service)
Red Teaming - How to simulate?
We will test the masquerading method used by the Rancor threat group’s Plaintee Trojan (Picus Threat ID: 206343).
C:\WINDOWS\system32>cmd.exe /c schtasks /create /sc MINUTE /mo 5 /tn "Windows Updata Services" /tr "\"%APPDATA%\Local Service.exe\" \"C:\PICUS_863a9199decf36895d5d7d148ce9fd622e825f393d7ebe7591b4d37ef3f5f677.dll\",OpenURLB" /F
SUCCESS: The scheduled task "Windows Updata Services" has successfully been created.As shown in the above figure, the Rancor group used Windows Updata Services as the name of the scheduled task. Note that they wrote updata instead of update.
Blue Teaming - How to detect?
Following Sigma rule can be used to detect scheduled task creation pointing to the %APPDATA% directory.
title: Suspicious Scheduled Task Creation Pointing to AppData
status: experimental
description: Detects the attempt to create a scheduled task pointing the %APPDATA% directory.
author: Picus Security
References: - https://attack.mitre.org/techniques/T1053/- https://attack.mitre.org/tactics/TA0002/
- https://attack.mitre.org/tactics/TA0003/
- https://attack.mitre.org/tactics/TA0004/
logsource:
category: process_creation
product: windows
detection:
selection:
Image: '*\schtasks.exe'
CommandLine: '* /create *AppData*'
filter:
User: NT AUTHORITY\SYSTEM
condition: selection and not filter
fields:
- CommandLine
- ParentCommandLine
tags:
- attack.persistence
- attack.privilege_escalation
- attack.execution
- attack.ta0002
- attack.ta0003
- attack.ta0004
- attack.t1053
falsepositives:
- Legitimate administrative activities
- Software installation
level: low3. Use a task name similar to a common software service (T1036.004 Masquerade Task or Service)
Red Teaming - How to simulate?
In this test, we will use Adobe Acrobat Reader Updater as the task name like the Turla threat group (Picus Threat ID: 141210).
C:\WINDOWS\system32>schtasks /Create /TR "%APPDATA%\Adobe\adobeup.exe" /SC WEEKLY /TN "Adobe Acrobat Reader Updater"
SUCCESS: The scheduled task "Adobe Acrobat Reader Updater" has successfully been created.Blue Teaming - How to detect?
Following Sigma rule is specific to the above masquerading method used by the Turla group. Moreover, you can use the Sigma rule given in the second exercise to detect this attack.
title: Suspicious Adobe Acrobat Reader Updater Scheduled Task Creation
status: stable
description: Detects the attempt to create a scheduled task called "Adobe Acrobat Reader Updater" which runs malicious backdoor (adobeup.exe). This technique is commonly utilized for persistence as Turla APT Group's usage in its threat campaigns.
author: Picus Security
references:
- https://attack.mitre.org/techniques/T1053/
- https://attack.mitre.org/groups/G0010/
- https://attack.mitre.org/tactics/TA0002/
- https://attack.mitre.org/tactics/TA0003/
- https://attack.mitre.org/tactics/TA0004/
logsource:
product: windows
service: security
definition1: 'Requirements: Group Policy : Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Detailed Tracking\Audit Process Creation'
definition2: 'Requirements: Group Policy : Computer Configuration\ Administrative Templates\ System\ Audit Process Creation\ Include Command Line'
detection:
selection:
EventID: 4688
NewProcessName: '*\schtasks.exe'
ProcessCommandLine: 'schtasks /Create *Adobe\\adobeup.exe\"* \"Adobe Acrobat Reader Updater\'
condition: selection
falsepositives:
- None
level: high
tags:
- attack.persistence
- attack.privilege_escalation
- attack.execution
- attack.ta0002
- attack.ta0003
- attack.ta0004
- attack.t1053
- attack.g0010Appendixes
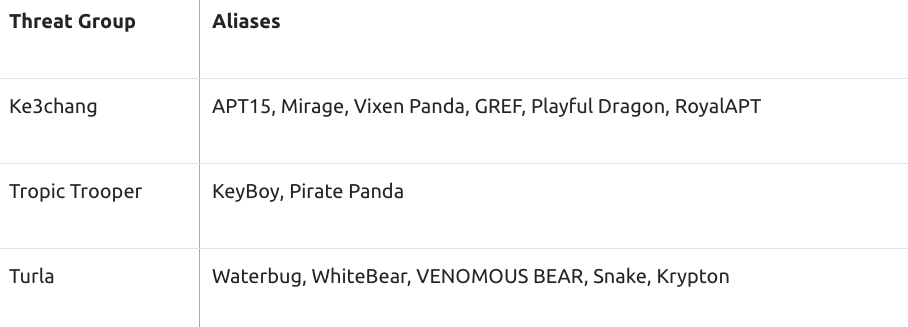
Appendix A - Aliases of Threat Groups
Appendix B - Aliases of Malware Families
Source: PICUS