Malware
- The Tech Platform

- Dec 11, 2020
- 8 min read
Malware, short for malicious software, is a blanket term for viruses, worms, trojans and other harmful computer programs hackers use to wreak destruction and gain access to sensitive information. As Microsoft puts it, "[malware] is a catch-all term to refer to any software designed to cause damage to a single computer, server, or computer network." In other words, software is identified as malware based on its intended use, rather than a particular technique or technology used to build it.
Types of malware
There are a number of different ways of categorizing malware; the first is by how the malicious software spreads. You've probably heard the words virus, trojan, and worm used interchangeably, but as Symantec explains, they describe three subtly different ways malware can infect target computers:
A worm is a standalone piece of malicious software that reproduces itself and spreads from computer to computer.
A virus is a piece of computer code that inserts itself within the code of another standalone program, then forces that program to take malicious action and spread itself.
A trojan is a program that cannot reproduce itself but masquerades as something the user wants and tricks them into activating it so it can do its damage and spread.
Spyware is defined by Webroot Cybersecurity as "malware used for the purpose of secretly gathering data on an unsuspecting user." In essence, it spies on your behavior as you use your computer, and on the data you send and receive, usually with the purpose of sending that information to a third party.
A keylogger is a specific kind of spyware that records all the keystrokes a user makes—great for stealing passwords.
A rootkit is, as described by TechTarget, "a program or, more often, a collection of software tools that gives a threat actor remote access to and control over a computer or other system." It gets its name because it's a kit of tools that (generally illicitly) gain root access (administrator-level control, in Unix terms) over the target system, and use that power to hide their presence.
Adware is malware that forces your browser to redirect to web advertisements, which often themselves seek to download further, even more malicious software. As The New York Times notes, adware often piggybacks onto tempting "free" programs like games or browser extensions.
Ransomware is a flavor of malware that encrypts your hard drive's files and demands a payment, usually in Bitcoin, in exchange for the decryption key. Several high-profile malware outbreaks of the last few years, such as Petya, are ransomware. Without the decryption key, it's mathematically impossible for victims to regain access to their files. So-called scareware is a sort of shadow version of ransomware; it claims to have taken control of your computer and demands a ransom, but actually is just using tricks like browser redirect loops to make it seem as if it's done more damage than it really has, and unlike ransomware can be relatively easily disabled.
Cryptojacking is another way attackers can force you to supply them with Bitcoin—only it works without you necessarily knowing. The crypto mining malware infects your computer and uses your CPU cycles to mine Bitcoin for your attacker's profit. The mining software may run in the background on your operating system or even as JavaScript in a browser window.
Malvertising is the use of legitimate ads or ad networks to covertly deliver malware to unsuspecting users’ computers. For example, a cybercriminal might pay to place an ad on a legitimate website. When a user clicks on the ad, code in the ad either redirects them to a malicious website or installs malware on their computer. In some cases, the malware embedded in an ad might execute automatically without any action from the user, a technique referred to as a “drive-by download.”
How to prevent malware
With spam and phishing email being the primary vector by which malware infects computers, the best way to prevent malware is make sure your email systems are locked down tight—and your users know how to spot danger. We recommend a combination of carefully checking attached documents and restricting potentially dangerous user behavior—as well as just familiarizing your users with common phishing scams so that their common sense can kick in.
When it comes to more technical preventative measures, there are a number of steps you can take, including keeping all your systems patched and updated, keeping an inventory of hardware so you know what you need to protect, and performing continuous vulnerability assessments on your infrastructure. When it comes to ransomware attacks in particular, one way to be prepared is to always make backups of your files, ensuring that you'll never need to pay a ransom to get them back if your hard drive is encrypted.
Malware protection
Antivirus software is the most widely known product in the category of malware protection products; despite "virus" being in the name, most offerings take on all forms of malware. While high-end security pros dismiss it as obsolete, it's still the backbone of basic anti-malware defense. Today's best antivirus software is from vendors Kaspersky Lab, Symantec and Trend Micro, according to recent tests by AV-TEST.
When it comes to more advanced corporate networks, endpoint security offerings provide defense in depth against malware. They provide not only the signature-based malware detection that you expect from antivirus, but anti-spyware, personal firewall, application control and other styles of host intrusion prevention. Gartner offers a list of its top picks in this space, which include products from Cylance, CrowdStrike, and Carbon Black.
How to detect malware
Step by step, do this now for all Windows computers:
Make sure your computer has an active connection to the internet.
Go to Sysinternals.com. It’s a Microsoft site.
Download Process Explorer and Autoruns. Both are free, as is everything on the site.
Unzip these programs. If using Process Explorer, use procexp.exe. If using Autoruns, use autoruns.exe (autorunsc.exe is the command-line version).
Right-click and run the program executable as Administrator, so it’s running in the Administrator’s security context.
Run Process Explorer first (I'll explain Autoruns later). Select the Options menu at the top of the screen.
Choose VirusTotals.com and Check VirusTotals.com.
This will submit all running executables to the VirusTotal website, which is run and maintained by Google. You’ll get a message to accept the license; answer Yes. You can close the VirusTotal website that comes up and go back to Process Explorer.
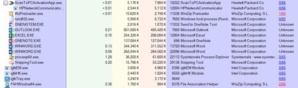
In Process Explorer, you'll see a column labeled Virus Total. It will either say Hash Submitted (during the first few seconds) or give you a ratio, something like 0/67, 1/67/ 14/66, and so on.
As you've probably guessed, the displayed VirusTotal ratio indicates how many antivirus engines at VirusTotal reported the submitted executable (hash) as malicious. Currently, the list of antivirus engines is 67, but it goes up and down all the time. I’m not sure why some executables are inspected by all of the antivirus engines and not others, but regardless of the denominator (lower number), if the numerator (above the line) is greater than zero you could have malware.
If it says 1/57 or 2/57, however, it probably isn’t malware, but a false positive instead. On the other hand, I've seen at least one real malware program that was detected by only one of the engines, so double-check to see if the name and vendor who created the program looks familiar. If not, it could be malicious. But in general, if the numerator is 1, I usually relax. If it’s 2, I investigate a little bit more. But even most of the 2s end up being false-positives. The next screenshot shows examples of two false-positives, both related to the legitimate vendor, Winzip Computing.
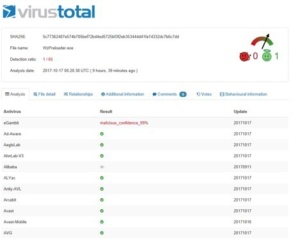
If you are not sure, simply click on the reported ratio, and it will take you to the VirusTotal page showing which AV engines did and didn’t report it as malware. VirusTotal also displays two symbols at the top of the page, one a red devil and the other a green smiley face wearing a halo. If the arrow is pointing to the green smiley face, which it usually is in these instances, that means VirusTotal’s experience leads them to classify the file as non-malicious. In the example screenshot below, even though the one “rogue” AV program (in this case, eGambit) itself claims to have 99 percent confidence that the file is malicious, none of the other 65 AV programs agree, and VirusTotal itself (as evidenced by the selected green smiley face) doesn’t agree.
So why would I recommend a program that often has false-positives? First, it’s an inherent problem with VirusTotal and not Process Explorer. Usually the false-positives are cleared up in hours as the AV vendor does its research and clean-up. And if you can overlook the possible minor false-positives that are easy to rule out, there is no single antivirus engine that is anywhere near as accurate as VirusTotal. It may make some minor mistakes erring on the side of caution, but it more than makes up for it in detecting the stuff that many other AV misses. It uses the power of 67 different AV engines against malware writers. Your antivirus product may miss something, but VirusTotal doesn’t.
Most malware programs are caught at a ratio with a numerator of 3 or higher (ex. 13/67). In fact, I’ve never had a false-positive when the numerator is 3 or higher. When I see anything at that numerator or higher, I right-click it in Process Explorer, note the file location path, and kill the process if I don’t absolutely recognize and trust the program file.
Then I manually delete the files associated with the executable — but proceed at your own risk! Be forewarned: This is always a chance you might accidentally delete something you need for some application or driver to run. If you’re worried, rename the file instead. That’s enough to stop the malware program from re-launching using that same file. I will usually rename it to something with a file extension ending in “thisismalware” so that I’ll remember what I did if I see it again. Usually if I’m not sure if the file I want to delete is malicious, I’ll rename the file, wait a week and then delete the file when I’m more sure that I didn’t impact anything legitimate.
Occasionally, malware will “fight” with you and not let you kill the process. If so, repeat the process above, but go with Autoruns instead. Use Autoruns to unselect the program so that it won't load at startup. Reboot and run Process Explorer again. Usually, the malware program will not be running and you can delete it. If using Autoruns doesn’t work and the file is still fighting you, you’ll have to boot into Safe Mode, find the executable and then delete or rename it. I haven’t run into an executable in years that fought me beyond this step, but it’s possible. If this happens, use VirusTotal to identify what antivirus products detect the target file as malicious, download it, and then run on your computer to get rid of the file. Heck, you might want this to be your first eradication step if you aren’t comfortable with manually killing and deleting files.
Put a shortcut to Process Explorer on your desktop. Always “Run as Administrator. I usually right-click the executable (not the desktop shortcut), choose Properties, then the Compatibility tab, select Change Settings for All Users, and then choose Run this program as an administrator. Make sure to run the 64-bit version if you run a 64-bit version of Windows. That is very common these days. I recommend that everyone download and run Process Explorer or Autoruns at least once a week. If that's too much, at least be sure to run it if your computer exhibits suspicious behavior.
Malware removal
How to remove malware once you're infected is in fact the million dollar question. Malware removal is a tricky business, and the method can vary depending on the type you're dealing with. CSO has information on how to remove or otherwise recover from rootkits, ransomware, and cryptojacking. We also have a guide to auditing your Windows registry to figure out how to move forward.
If you're looking for tools for cleansing your system, Tech Radar has a good roundup of free offerings, which contains some familiar names from the antivirus world along with newcomers like Malwarebytes.
Source: Whatls







Comments