How to Disable NTLM Authentication in Windows Domain
- The Tech Platform

- May 30, 2021
- 2 min read
Updated: Mar 23, 2023
NTLM authentication is a Microsoft Windows protocol used for authentication purposes in Windows domain networks. It is used to authenticate user identities and provide secure access to network resources such as servers, printers, and file shares. In this article, we will guide you on how to Disable NTLM Authentication in Windows Domain
What is NTLM Authentication?
NTLM stands for "NT LAN Manager", which is the name of the authentication protocol used by Windows NT operating systems. NTLM authentication is based on a challenge-response mechanism, where the server sends a challenge to the client, and the client responds with a hash of the user's password. The server then compares the hash with the one it has stored for that user, and if they match, the authentication is successful.
NTLM authentication is still widely used in Windows domains, but it has been superseded by Kerberos authentication in newer versions of Windows. Kerberos is a more secure authentication protocol that provides mutual authentication between the client and server and uses encryption to protect the authentication process.
There can be multiple reasons why you may want to disable NTML Authentication in Windows Domain.
Some of the most common reasons are:
NTML is not secure and offers weak encryption.
In the case of NTML, your password hash will be stored in LSA Service. It can be easily extracted by an attacker.
It is vulnerable to Data Interception attacks as there is a lack of mutual authentication between the client and the server.
Disable NTML Authentication in Windows Domain
These are the ways by which we are going to disable NTML Authentication in Windows Domain
Using Local Group Policy Editor
Using Registry Editor
Method 1: Using Group Policy Editor
Before disabling NTML, we need to make sure that you are not using its most unprotected protocol i.e; NTMLv1 or NTML Version 1. This can make your domain vulnerable to attackers. Once you are done with that, follow the following method to disable NTML Authentication in Windows Domain by Group Policy Editor.
STEP 1: Press the Windows key + R. Type gpedit.msc and press Enter.
STEP 2: Navigate the following path:
Computer Configuration > Windows Settings > Security Settings > Local Policies > Security OptionsSTEP 3: Now, double-click on 'Network Security: LAN Manager authentication level'.

STEP 4: Select Sent NTMLv2 response only. Refuse LM & NTML from the “Local Security Settings” tab.

STEP 5: Click Apply followed by Ok.
NTML authentication will be disabled on your domain.
Method 2: Using Registry Editor
You can also disable NTML from the Registry Editor. Follow the below steps to do so:
STEP 1: Press the Windows key + R. Type 'regedit.exe' and press Enter.
STEP 2: Navigate to the following location.
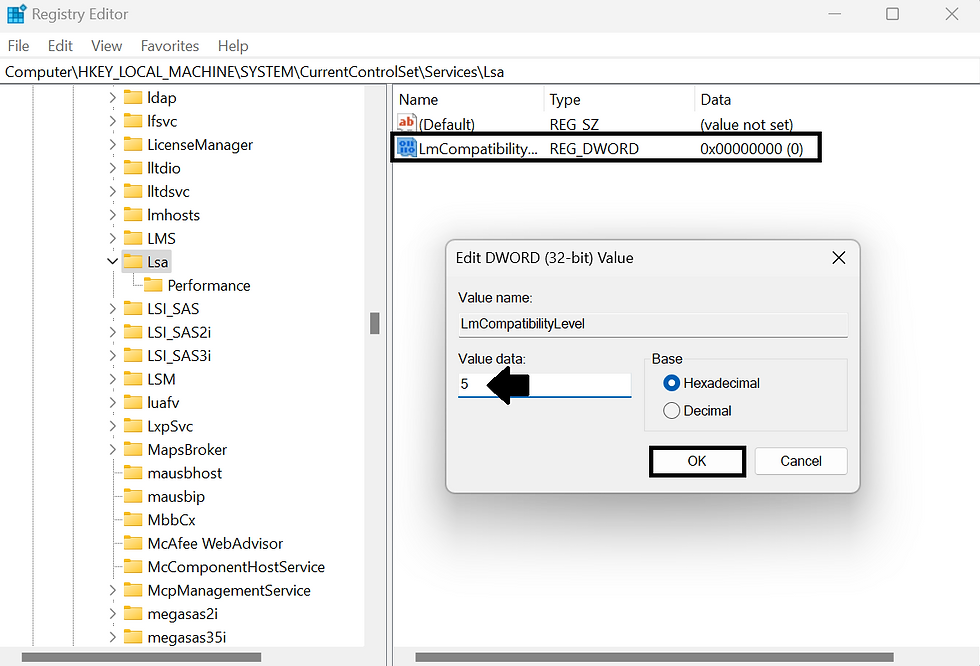
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LsaSTEP 3: Now, right-click on Lsa and select New => DWORD (32-bit) Value. Type “LmCompatibilityLevel” and click OK.
The registry key is created.

Now, double-click on the registry key and set the Value data to 5.
5 because it corresponds to “Sent NTMLv2 response only. Refuse LM & NTML”.
STEP 4: Close the Registry Editor Window and restart your PC to apply the changes.
That's It!




Comments