How does two step verification works
- The Tech Platform

- May 13, 2022
- 4 min read
Two-factor authentication (2FA) is a security process in which users provide two different authentication factors to verify themselves. It is implemented to better protect both a user's credentials and the resources the user can access. Two-factor authentication provides a higher level of security than authentication methods that depend on single-factor authentication (SFA), in which the user provides only one factor -- typically, a password or passcode. Two-factor authentication methods rely on a user providing a password as the first factor and a second, different factor -- usually either a security token or a biometric factor, such as a fingerprint or facial scan.

Source: google
Types of Two Step Verification:
Two step verification can either be:
Single factor 2SV — An example of this would be using your username/password as the first step and then an OTP you receive via an SMS text message.
Two factor 2SV — An example of this would be using your username/password combination as the first step and then a second factor (such as a randomly generated code from a cryptographic USB token) as the second step.
Authentication factors?
There are several ways in which someone can be authenticated using more than one authentication method. Currently, most authentication methods rely on knowledge factors, such as a traditional password, while two-factor authentication methods add either a possession factor or an inherence factor.
Authentication factors, listed in approximate order of adoption for computing, include the following:
A knowledge factor is something the user knows, such as a password, a personal identification number (PIN) or some other type of shared secret.
A possession factor is something the user has, such as an ID card, a security token, a cellphone, a mobile device or a smartphone app, to approve authentication requests.
A biometric factor, also known as an inherence factor, is something inherent in the user's physical self. These may be personal attributes mapped from physical characteristics, such as fingerprints authenticated through a fingerprint reader. Other commonly used inherence factors include facial and voice recognition or behavioral biometrics, such as keystroke dynamics, gait or speech patterns.
A location factor is usually denoted by the location from which an authentication attempt is being made. This can be enforced by limiting authentication attempts to specific devices in a particular location or by tracking the geographic source of an authentication attempt based on the source Internet Protocol address or some other geolocation information, such as Global Positioning System (GPS) data, derived from the user's mobile phone or other device.
A time factor restricts user authentication to a specific time window in which logging on is permitted and restricts access to the system outside of that window.
How Does Two-Factor Authentication Work?
Here’s a quick rundown of what adding 2FA to an account looks like for the methods described above.
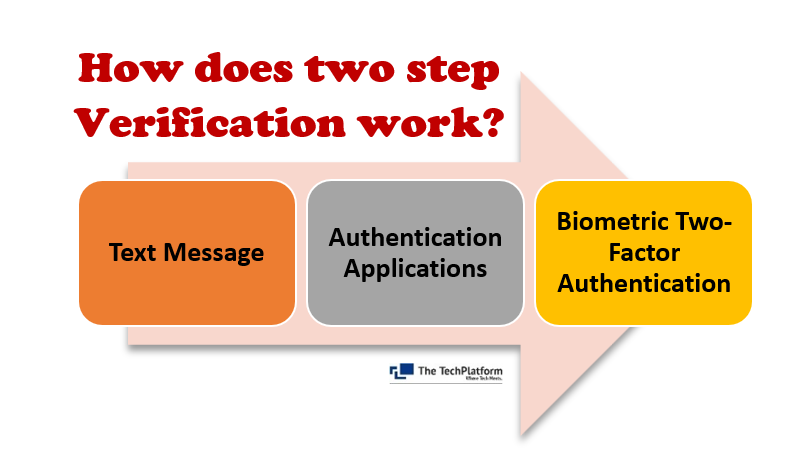
1. Text Message
Text messages for two-factor authentication send a login code to a mobile device number you register with the account. This is the most streamlined form of 2FA. All you need is a cellphone and a connection to a wireless network. Text message 2FA is very common for personal accounts, but it is not without risk. There is a chance someone can impersonate you to the phone company, hijack your phone, and gain unauthorized access to your accounts. Corporations should be wary of this method unless employees have dedicated corporate phone lines. Routing access through an employee’s personal number risks a fired employee doing major damage.
In addition, employees’ personal phone plans may not offer service everywhere, which risks an employee locking themselves out of their accounts while on an international business trip.
2. Authentication Applications
Authentication app 2FA works by using a mobile app to generate an authentication code. You must then enter this code to gain access to your account. Unlike text messages, apps don’t require the user to have access to a wireless network. Any internet connection is enough to access your account.
In addition, authentication apps like Google offer a list of backup codes to use in case of connectivity problems.
3. Biometric Two-factor Authentication
Biometric 2FA works by requiring you to present something unique to your physical person to gain access to your account. Common methods of biometric verification include retina scans by your computer’s camera, or a requirement to use your fingerprint on your tablet.
While increasingly popular, it’s important to note limitations to these methods exist. The most common is the fear of biometric data theft. Unlike a changeable password, stealing information about your retina or fingerprint would comprise your security and privacy for life.
Advantages of 2FV:
2 Step Verification provides strong security which reduces the chances of hackers trying to hack or access our device.
It provides productivity and flexibility to people so that they can easily access their sensitive data without putting it at risk.
Two-Step Verification provides an easy way for people to change their password easily and get a good opportunity to create products for any company/own.
It redirects fraud and establishes a secure online relationship that allows people to easily access online marketing apps on these networking sites.
Disadvantages of 2FV:
The factor can get lost! whenever you need and if you do a mistake, then you guys are logged out from there.
False Security! When you’re trying to log in to your account and if you do a mistake then you will be logged out from there because two-step verification identifies you as a hacker. And if you logged in to your account without any factor then a hacker too.
The two-step verification is only effective when you take great care of your account security. That is why it is necessary that you also choose a difficult hue to login into your account.
The Tech Platform




Comments