Cyber Threat Intelligence (CTI) in a Nutshell — 1
- The Tech Platform

- Oct 20, 2020
- 7 min read
Hackers are working to stay ahead of security programs and find new ways to break through organizations’ networks, so it is important that security experts use proactive best practices to prevent incidents.
Like intelligence, it provides valuable cyber threats — additional cyber threat information that reduces uncertainty and helps consumers identify threats and opportunities.
Hackers are working to stay ahead of security programs and find new ways to break through organizations’ networks, so it is important that security experts use proactive best practices to prevent incidents. One of the best ways to do this is to understand and evaluate information about your organization’s cyber threats, and then apply that knowledge to ongoing efforts. With the right cyber threats, intelligence is present, you can take every step towards as good cybersecurity as possible.
Cyber threat information refers to the data that organizations collect and use to better understand past, present, and future threats. The information collected provides context to the operations on an organization’s network and helps identify potential threats and remain protected from future attacks. Organizations need to understand the attacker’s next steps so they can proactively defend their sensitive data and prevent future attacks.
ENISA
CTI provides information on malicious actors, their tools, their infrastructure, and their methods for;
● Identifying types of attacks,
● Defining, guiding, and prioritizing operational requirements,
● Understanding threat actor capability, tactics, techniques, and procedures,
● Deploying detection systems,
● Developing defense strategies.
Even though more can be added, we can classify the top threats as follow;
● Malware,
● Web-based attacks,
● Web application attacks,
● Denial of Service,
● Botnets,
● Phishing,
● Spam,
● Ransomware,
● Insider threat,
● Physical manipulation/damage/theft/loss,
● Exploit kits,
● Data breaches,
● Identity theft,
● Information leakage,
● Advanced Persistent Threats (APTs)
To be able to prevent or minimize the risks against such threats, it is important to understand, analyze and being advanced in five methods of threat detection and response;
(1) Network and endpoint monitoring that is constant and comprehensive, including capabilities such as full-packet capture and behavior-based threat detection on hosts.
(2) Advanced analytics techniques that can sift through massive amounts of information, such as network traffic, in near-real-time to spot suspicious behaviors and accelerate investigations.
(3) Malware analysis using methods that don’t rely on file signatures and go straight to the actual behavior of executables, whether collected on the network or endpoints, to detect hostile activity.
(4) Incident detection and response practices that align security personnel, processes, and technologies to streamline and accelerate workflows so security operations teams can spend less time on routine tasks and more time defending high-priority assets and address the riskiest threats.
(5) Open-source intelligence (OSINT) is collecting information from the public, open tools, or resources to be used in an intelligence context. Data flow for OSINT can be categorized into 6 classifications. Media (newspapers, magazines, radio, television, etc.), Internet (such as blogs, dark-web, websites, YouTube, Twitter, Facebook, etc.), Public Government Data (public government reports, speeches, conferences, etc.), Professional and Academic Publications (journal, academic papers, dissertation, theses, etc.), Commercial Data (commercial imagery, financial and industrial assessments, etc.), Grey Literature (technical reports, preprints, patents, business documents, etc.).
A. The Methodology of Cyber Attacks
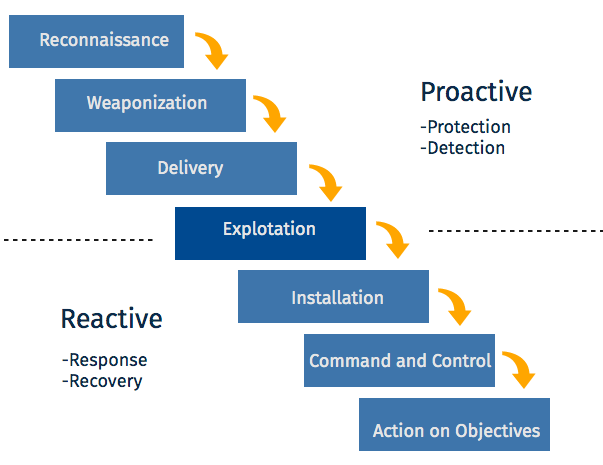
Figure 1 depicts 7 phases of a cyber-attack aka Lockheed Martin’s “Cyber Kill Chain”. These attack steps were also presented in NIST SP 800–115.
Figure 1 — Cyber Kill Chian
By following cyber kill chain steps, an adversary can;
(1) identify and select a target(s) (Phase 1 — Reconnaissance),
(2) packages an exploit into a payload designed to execute on the targeted computer/network (Phase 2 — Weaponize),
(3) delivers the payload to the target system(s) (Phase 3 — Deliver),
(4) executes the code on the target system(s) (Phase 4 — Exploit),
(5) installs remote access software that provides a persistent presence within the targeted environment or system (Phase 5 — Install),
(6) employs remote access mechanisms to establish a command and control channel with the compromised device (Phase 6 — Command and Control),
(7) pursues intended objectives (e.g., data exfiltration, lateral movement to other targets) (Phase 7 — Act on Objectives).
Perceiving that a progression of preliminary steps and activities will go before a malicious attack, intelligence efforts can be sent to recognize;
● who may be targeting a network?
● what are the intentions and capabilities of the malicious actors?
● when they will conduct their activity?
● where the activity will originate?
● how they plan to penetrate or affect the network?
B. Characteristics of Cyber Threat Intelligence
By perceiving and drawing in the enemy amid the reconnaissance, weaponization, and conveyance periods of the cyber-attack lifecycle, can give a chance to time to take the necessary course of action to protect the network and prevent the attacks. This also allows for creating an effective response and recovery strategies. To be more effective in threat intelligence, the following characteristic should be adapted;
● Timely: For effective threat intelligence time plays a critical role. Intelligence ought to be quickly conveyed with insignificant idleness.
● Relevant: Threat intelligence needs to apply to the related environment.
● Accurate: To be able to take more reasonable and effective measurements against attacks more accurate intelligence is necessary. Therefore, the information which is provided by threat intelligence should be correct, complete, and explicit.
● Specific: More detailed and more specific threat intelligence can allow defenders to choose suitable countermeasures.
● Actionable: Actions are needed to be identified by threat intelligence to ensure necessary data for the response against threats.
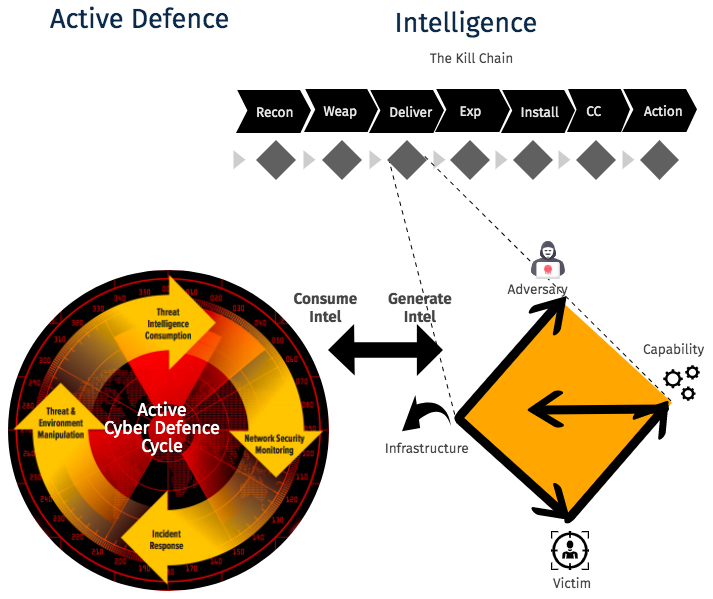
One other recommended intelligence model is named as the Diamond Model of Intrusion Analysis. The model verbalizes and investigates the four key purposes of any occasion: adversary, infrastructure, capability, and victim. Understanding these four purposes of the model, finding the data identified with each, and understanding wherein the attacker’s kill chain the occasion happened fundamentally adds to understanding an attacker and in like manner delivering threat intelligence.
The Cyber Kill Chain and the Diamond Model help to distinguish intrusions and look past the possibility of a solitary intrusion and toward identification and understanding of attacker techniques. Both of these nourish into the Active Cyber Defense Cycle as shown in figure 2.
Figure 2 — The Continual Process of Generating and Consuming Intelligence for Hunting Threats
C. Cyber Threat Hunting
Cyber threat hunting is the procedure of proactively and iteratively seeking through networks to detect and isolate propelled threats that avoid existing security arrangements. Hunting is an iterative procedure, which means it must be consistently done in a loop, starting with a hypothesis. There are three types of hypotheses;
● Analytics-Driven: “Machine-learning and UEBA (Unlike rule-based systems), used to develop aggregated risk scores that can also serve as hunting hypotheses”.
● Situational-Awareness Driven: “Crown Jewel analysis, enterprise risk assessments, company- or employee-level trends”.
● Intelligence-Driven: “Threat intelligence reports, threat intelligence feeds, malware analysis, vulnerability scans”.
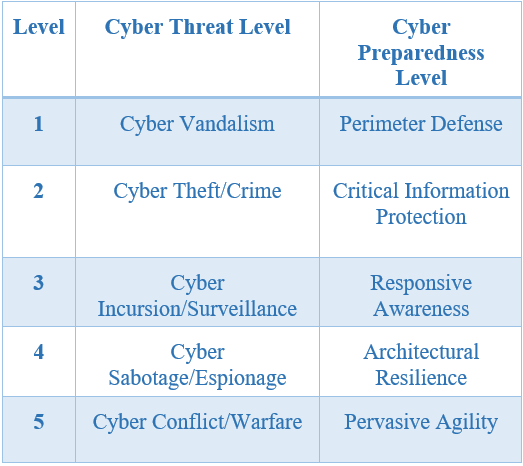
D. Cyber Threat Levels
Cyber threat and preparedness levels were introduced by the MITRE Corp. Five cyber threat levels were proposed and each of which corresponds to a general strategy of cyber defense as it is shown in table 1.
Table 1 — Cyber Threat and Preparedness Levels
● Threat-Level-1: Cyber Vandalism, which corresponds to Perimeter Defense
● Threat-Level-2: Cyber Theft/Crime, which corresponds to a defense approach of Critical Information Protection
● Threat-Level-3: Cyber Incursion/Surveillance, which corresponds to a defense approach of Responsive Awareness
● Threat-Level-4: Cyber Sabotage/Espionage, which corresponds to a defense approach of Architectural Resilience
● Threat-Level-5: Cyber Conflict/Warfare, which corresponds to a defense approach of Pervasive Agility.
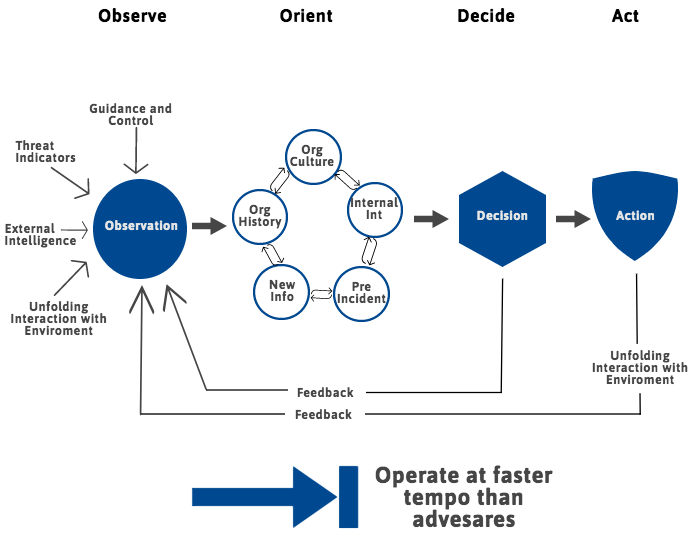
E. Cyber Threat Management
Cyber Threat Management (CTM) is much more than just risk assessment. It emerges best practices for managing cyber threats. CTM includes:
● Manual and automated intelligence gathering and threat analytics.
● A comprehensive methodology for real-time monitoring including advanced techniques such as behavioral modeling.
● Use of advanced analytics to optimize intelligence, generate security intelligence, and provide Situational Awareness.
● Technology and skilled people leveraging situational awareness to enable rapid decisions and automated or manual actions.
The cyber threat management framework (as shown in figure 3) has different stages such as Observation, Orientation, Decision, Action which can help early detection of threats and limit damage actions.
Figure 3 — Cyber Threat Management Framework
Automated security systems can use threat information to protect networks and systems by tracking threat vectors such as network traffic, network activity, and network connectivity. Once a specific threat vector is identified and added to the data feed, it becomes much easier for firewalls and SIEM Security Information and Event Management) applications to identify and block it. That is why it is essential to combine cyber-threat intelligence tools with up-to-date threat information feeds that provide data on emerging and existing threats.
This information helps security teams to learn about the tactics, techniques, and practices of potential hackers and can be used to improve the security of their systems when working properly. Coupled with a robust security solution, threat information can help reduce vulnerability to cyber-attacks and save your business money by avoiding recovery-related expenses, including money that can be paid as a penalty or as part of legal action. Effective security programs require continuous monitoring and evaluation to ensure that threat information works in conjunction with other security solutions.
Through this process, raw data becomes a valuable resource for the security team and an important part of the overall security strategy. Once you have put in place these basic measures, it is up to you to keep your security teams up to date with the latest cyber threats and best practices in cybersecurity. Applying the insights gained from this data allows your security team to make faster and more informed security decisions, so you are one step ahead of any cyber threat.
Threat information is useful in many ways, the most important being to help security professionals understand the attacker’s thought process by uncovering the motives behind the attack and the behavior of the threat. With the external insights and context that threat intelligence provides, your vulnerability management team can prioritize the more important vulnerabilities more accurately.
Cyber threat intelligence provides knowledge to bring unknown threats to light, enabling organizations to make better decisions about their security. Keep stakeholders, executives and users informed about the latest cyber threats and their impact on your organization. Make sure that your security team is kept informed of the enormous volume of cyber threats, including the methods used.
One of the ways organizations do this is to integrate intelligence feeds on cyber threats into their existing security solutions. This is a collection of information from various sources coming from across the network and gives a sense of potential global threats that can be as simple as suspicious domains and IP addresses associated with suspicious activity.
Source: Medium.com












Comments